The Only Guide for Aws S3 Backup
Top Guidelines Of Protection Against Ransomware
Table of ContentsSome Of S3 BackupThe Ultimate Guide To S3 Backup8 Simple Techniques For Rto6 Simple Techniques For S3 Cloud BackupWhat Does Ec2 Backup Mean?Our Aws Cloud Backup PDFs
The GDPR highlights the personal information civil liberties of EU homeowners, including the right to transform, gain access to, get rid of, or transfer their information. Personal data refers to any kind of info that connects to an individual.
To maintain their information available in all times, companies need to keep the IT infrastructure energetic even when it comes to a disaster. This state of surefire access to information is known as information availability. This article reviews the essentials of data schedule as well as its obstacles, as well as offers methods to maintain a high level of information accessibility.
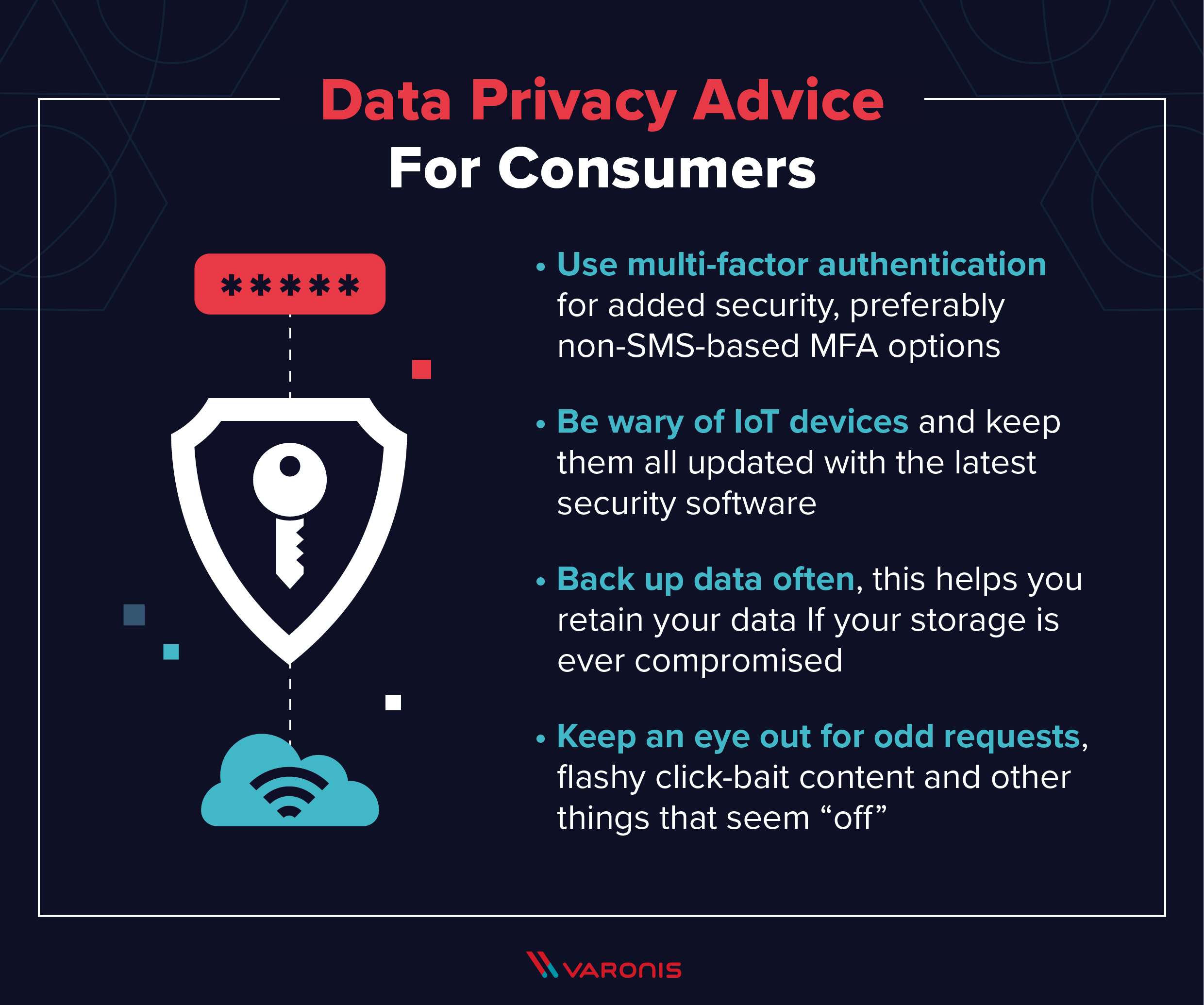
Without an appropriate information security policy, delicate information can fall under the hands of assailants, allowing them to get to your network, and also expose the personal information of consumers as well as employees. This post presents the principle of information safety and security as well as the various devices and also approaches you can use to shield your data and also prevent a catastrophe.
The 7-Minute Rule for Data Protection
Security makes sure the integrity of information by securing it from unauthorized alteration. File encryption minimizes the danger of accessing data from unreliable sources by validating data's resource.
A continuous information defense system preserves a document of all information adjustments and allows you to recover a system to any type of previous point. This kind of back-up fixes the trouble of losing data developed between 2 scheduled backups. It additionally gives protection against assaults like ransomware or malware, in addition to unintentional removal of information.
Any type of firm that refines and stores personal information of EU people, also if it is not physically located in the EU, should use to the GDPR rules. There are two primary duties in the GDPR: the GDPR Information Cpu is an entity that holds or refines this sort of information in support of one more organization, as well as a GDPR Data Controller that collects or processes personal data for its own purposes.
Object Lock stops item version deletion during a user-defined retention period. Immutable S3 things are secured making use of item, or bucket-level arrangement of WORM and also retention attributes. This functionality provides both data security, including additional protection against unexpected or harmful deletion as well as ransomware and also governing compliance. Read more: S3 Things Lock Protecting Information for Ransomware Hazards and also Conformity The cloud-based membership of Workplace 365 allows employees to work anywhere, anytime without the demand to organize their very own content as well as emails.
The Ultimate Guide To Ransomware Protection

Data security is the process of safeguarding crucial details from corruption, concession or loss. The importance of data protection boosts as the quantity of information developed and also stored proceeds to expand at extraordinary rates. There is likewise little resistance for downtime that can make it difficult to access crucial information.

The vital concepts of information defense are to safeguard and also provide data under all scenarios. The term information protection explains both the functional back-up of data as well as organization continuity/disaster healing (BCDR). Information defense strategies are advancing along two lines: information accessibility as well as data administration. Data availability makes sure individuals have the data they need to conduct service even if the information is damaged or shed.
The 25-Second Trick For Ec2 Backup
Information lifecycle management is the process of automating the movement of critical data to online and also offline storage. Information lifecycle administration is a detailed technique for valuing, cataloging and also protecting info properties from application as well as individual mistakes, malware and virus strikes, device failing or center interruptions and also disturbances. More just recently, information monitoring has come to consist of locating means to unlock company value from or else inactive duplicates of data for coverage, test/dev enablement, analytics and other functions.
(CDP) backs up all the information in a venture whenever a modification is made. Information portability-- the capability to relocate data amongst various application programs, computing atmospheres or cloud services-- provides an additional collection of problems as well as solutions for information defense.
Some Known Details About Data Protection
Information defense is the process of safeguarding important details from corruption, concession or loss. The importance of information security boosts as the amount of data created and also saved proceeds to grow at unprecedented prices. There is additionally discover here little resistance for downtime that can make it impossible to accessibility essential details (https://www.allmyfaves.com/clumi0/).
Protecting information from concession and making certain information personal privacy are other essential parts of data defense. The coronavirus pandemic triggered millions of workers to work from house, causing the requirement for remote information security. Organizations have to adapt to ensure they are protecting data anywhere employees are, from a main data facility in the workplace to laptop computers in your home.
The vital principles of data security are to safeguard and make offered data under all scenarios - https://www.tumblr.com/clumi0.
Information lifecycle administration is an extensive strategy for valuing, cataloging and safeguarding details possessions from application as well as user mistakes, malware and also virus assaults, machine failing or facility outages and disturbances. Much more lately, information administration has actually come to consist of discovering ways to unlock organization value from or else inactive duplicates of information for reporting, test/dev enablement, analytics as well as various other objectives.
The Buzz on Ec2 Backup
(CDP) backs up all the information in a venture whenever an adjustment is made. Data transportability-- the ability to relocate data amongst different application programs, calculating atmospheres or cloud services-- provides an additional set of problems as well as solutions for data defense.